The Comprehensive Engineering and Operational Report on Bypassing the Ford Passive Anti-Theft System (PATS): Architectures, Protocols, and Recovery Methodology
The automotive security landscape underwent a seismic shift in the mid-1990s with the widespread adoption of transponder-based immobilization. For Ford Motor Company, this initiative materialized as the Passive Anti-Theft System (PATS), commercially branded as SecuriLock. This system fundamentally altered the mechanics of vehicle ignition from a purely electrical circuit—susceptible to mechanical manipulation or “hotwiring”—to a sophisticated digital handshake involving cryptographic authentication between an embedded Radio Frequency Identification (RFID) chip and the vehicle’s Powertrain Control Module (PCM).
This report serves as an exhaustive technical resource for automotive technicians, security researchers, and advanced enthusiasts facing the “All Keys Lost” (AKL) scenario. It deconstructs the engineering architecture of PATS across its five generational iterations, delineating the impossibility of analog bypass methods such as the “resistor hack” and establishing the necessity of digital intervention. Through a rigorous analysis of forensic data,
wiring diagrams, and diagnostic protocols, this document validates legitimate software-based recovery methods utilizing tools like FORScan and IDS, while also examining the efficacy and risks of aftermarket hardware bypass modules from manufacturers such as Fortin and Directed Electronics. Furthermore, it integrates critical insights into the legal, insurance, and warranty implications of bypassing factory security, ensuring a holistic understanding of the recovery process.
Ford PATS Bypass Guide
How to handle a “Lost All Keys” situation, bypass the immobilizer, and get your engine running without a tow truck.
Understanding the “No Start” Condition
The Passive Anti-Theft System (PATS), also known as SecuriLock, disables your Ford’s fuel injectors or starter if a recognized transponder key isn’t detected. If you’ve lost your keys, or are performing an engine swap, bypassing this system is a critical hurdle.
Reality Check: “Bypassing” without a key usually means programming a new key or flashing the ECU. Hotwiring is impossible on modern PATS vehicles because the ECU requires a digital handshake.
Cost Analysis: Fix vs. Bypass
Comparing the financial impact of different solutions for a standard Ford F-150 (2004-2014 era). Dealer prices include towing.
Analysis
While a > is the most cost-effective (~$50 for the adapter), it requires a steep learning curve. The “PATS Delete” (ECU Flash) is effective for engine swaps but costs more than simply hiring a mobile locksmith for a standard lost key situation.
Difficulty by Model Year
Ford security has evolved. What worked on a 1998 Mustang will not work on a 2018 F-150.
The “Golden Era” of Bypass
Vehicles between 1996-2010 are the easiest to bypass or reprogram. Post-2011, Ford introduced higher-bit encryption (80-bit) and BCM integration, significantly lowering the success rate of cheap bypass modules and simple tricks.
Which Method Works For You?
Do you have a physical key that turns the ignition?
(Even if it’s not programmed)
OBD Programming
Use FORScan + ELM327 Adapter.
Cost: Low | Time: 20 mins
Success
System learns new key ID. Car starts.
Mechanical Barrier
Ignition cylinder is locked.
Drill or Locksmith
You must physically replace the cylinder or have a key cut by VIN code before bypassing electronics.
Method Trade-offs: Risk vs. Reward
Comparing major solutions. X-Axis: Cost ($). Y-Axis: Technical Skill Required (1-10). Bubble Size: Time Required (Hours).
1. FORScan (The DIY King)
FORScan is software that can access Ford’s proprietary modules. With an “Extended License” (often free), you can enter the PATS programming mode.
- Requires: PC laptop, ELM327 OBDII adapter.
- Wait time: 10-12 minute security delay is normal.
- Verdict: Best for “Lost All Keys” on 2000-2016 models.
2. Remote Start Bypass
Modules like the Fortin or Directed interfaces are designed for remote starters but can permanently bypass PATS if wired correctly (“Key Wrap” method).
- Requires: Wiring skills, usually one valid key to program the module initially.
- Verdict: Good for modified cars, but hard if you have zero keys.
3. PATS Delete (ECU Tune)
Using tuners like HP Tuners to toggle the PATS switch in the PCM firmware to “Disable”.
- Requires: Expensive hardware ($300+) or sending ECU by mail.
- Verdict: Essential for engine swaps (e.g., Coyote swap into a Foxbody).
Critical FAQs
Can I just cut a wire to bypass PATS?
No. On nearly all Fords after 1996, the PATS system cuts the fuel injectors via the PCM. Cutting wires will simply ensure the car never starts. It is a data-driven system, not a simple 12V relay circuit.
Does the “30-Minute Relearn” work?
On some older GM vehicles (Passlock), yes. On Ford? Generally no, unless you are adding a third key when you already have two. For “Lost All Keys,” you typically need diagnostic tools to reset the parameter count.
Where can I find my Key Code?
See our guide on >. The blinking pattern of the theft light often tells you why the bypass failed (e.g., Code 13: Key code not received).
© 2026 FordMasterX Infographics. Data sourced from manufacturer owner manuals.
The Evolution of Automotive Immobilization
The Death of Hotwiring
For decades, the concept of "hotwiring" a vehicle was a staple of cinema and automotive lore. In simplified terms, hotwiring involved physically bridging the battery ignition wire to the starter solenoid wire, bypassing the mechanical lock cylinder to crank the engine. In older vehicles, once the engine cranked and the ignition coil received power, the engine would run. The introduction of PATS effectively rendered this method obsolete for Ford vehicles manufactured after 1996.
PATS introduces a digital gatekeeper into the ignition sequence. While a thief might successfully force the ignition cylinder to turn or jump the starter relay to crank the engine, the fuel injectors and ignition coils remain electronically disabled by the PCM. Without the correct cryptographic signature from a paired transponder, the engine acts as an inert air pump—cranking endlessly but never achieving combustion. This distinction between "cranking" and "starting" is the primary diagnostic indicator of a PATS intervention.
Distinction Between RKE and PATS
A critical point of confusion for many vehicle owners and novice technicians is the difference between the Remote Keyless Entry (RKE) system and the Passive Anti-Theft System (PATS). As elucidated in recent technical documentation regarding Ford F-150 Key Fob Programming, these are two separate subsystems that often share the same physical key housing but operate on independent circuits.
- Remote Keyless Entry (RKE): This system controls convenience features such as door locks, trunk release, and the panic alarm. It operates via a battery-powered radio transmitter (fob) sending a UHF signal (typically 315 MHz or 433 MHz) to the Body Control Module (BCM) or a dedicated Generic Electronic Module (GEM). Programming the RKE buttons (often done via a customized ignition cycling sequence, such as turning the key 8 times) does not program the transponder chip required to start the engine.2
- Passive Anti-Theft System (PATS): This is the immobilizer. It relies on a passive RFID pellet embedded in the key head. This pellet requires no battery; it is energized inductively by the transceiver ring around the ignition. A key can have a dead battery and still start the car, provided the transponder chip is intact and programmed. Conversely, a key can unlock the doors (RKE) but fail to start the car if the chip is unprogrammed.
The Engineering Architecture of Ford PATS (SecuriLock)
The Physics of RFID Induction
At the heart of the PATS system lies the physics of magnetic induction. The system comprises four primary components: the Transponder Key, the Transceiver (Antenna Ring), the Control Module (Cluster, BCM, or SCIL), and the Powertrain Control Module (PCM).
When the driver inserts the key and turns the ignition to the RUN position, the Transceiver—a copper coil loop encasing the ignition lock cylinder—is energized by the vehicle's electrical system. This coil emits a low-frequency electromagnetic field, typically oscillating at 134.2 kHz.
The key contains a small glass or carbon-encased capsule (the transponder) consisting of a microchip and a copper coil. When this capsule enters the transceiver's magnetic field, the coil within the key generates a small electrical current via induction. This current powers up the microchip, which then modulates the magnetic field to transmit its unique hexadecimal identifier (ID) back to the transceiver. This process is known as Load Modulation.
Generational Architectures
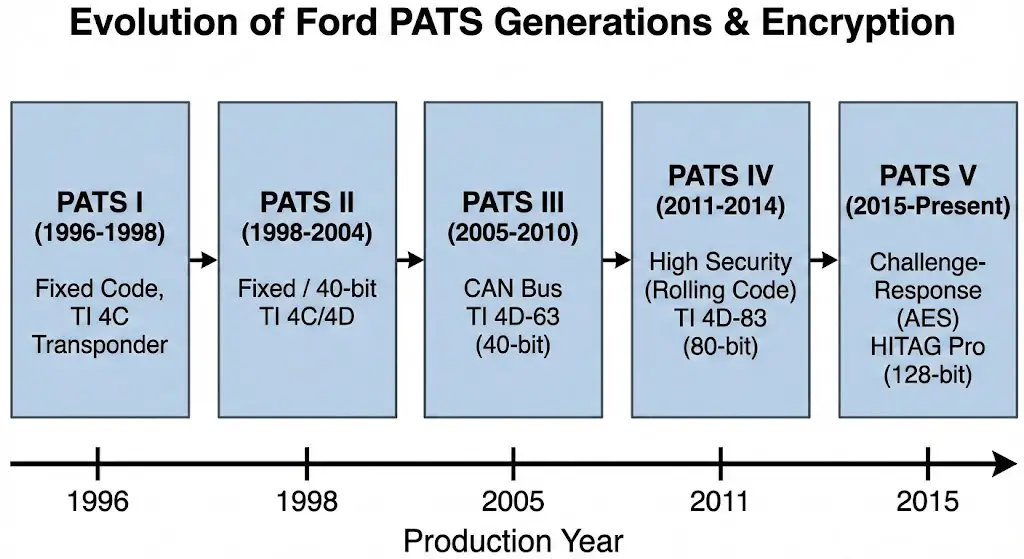
Ford's implementation of PATS has evolved through several distinct generations, each increasing in integration and cryptographic complexity. Understanding the generation is vital for selecting the correct bypass or programming method.
| Generation | Production Era | Control Module Location | Transponder Type | Encryption Protocol |
| PATS I | 1996–1998 | Standalone Module | Texas Instruments 4C | Fixed Code |
| PATS II | 1998–2004 | HEC (Cluster) or PCM | Texas Instruments 4C/4D | Fixed / 40-bit |
| PATS III | 2005–2010 | Instrument Cluster / PCM | TI 4D-63 (40-bit) | CAN Bus Communication |
| PATS IV | 2011–2014 | Body Control Module (BCM) | TI 4D-83 (80-bit) | High Security (Rolling Code) |
| PATS V | 2015–Present | BCM / PEPS (Push Start) | HITAG Pro / 128-bit | Challenge-Response (AES) |
The Pre-CAN Era (PATS I & II)
In early iterations found in vehicles like the 1999 Ford F-150 or the Ford Ranger, the PATS logic was often housed in a standalone module or integrated into the Hybrid Electronic Cluster (HEC). The communication between the transceiver and the module occurred over dedicated TX/RX lines. If the module validated the key, it sent a "Go" signal to the PCM via the SCP (Standard Corporate Protocol) bus.
The CAN Bus Era (PATS III, IV, & V)
With the advent of the Controller Area Network (CAN), the architecture shifted. In vehicles like the 2012 Ford Fusion or 2014 F-150, the transceiver signal is digitized by the Instrument Panel Cluster (IPC) or Body Control Module (BCM) and broadcast over the High-Speed CAN bus to the PCM. This integration makes "hotwiring" effectively impossible because bypassing the lock cylinder does not generate the necessary encrypted CAN messages required to unlock the fuel injectors.
The Logic Chain of Immobilization
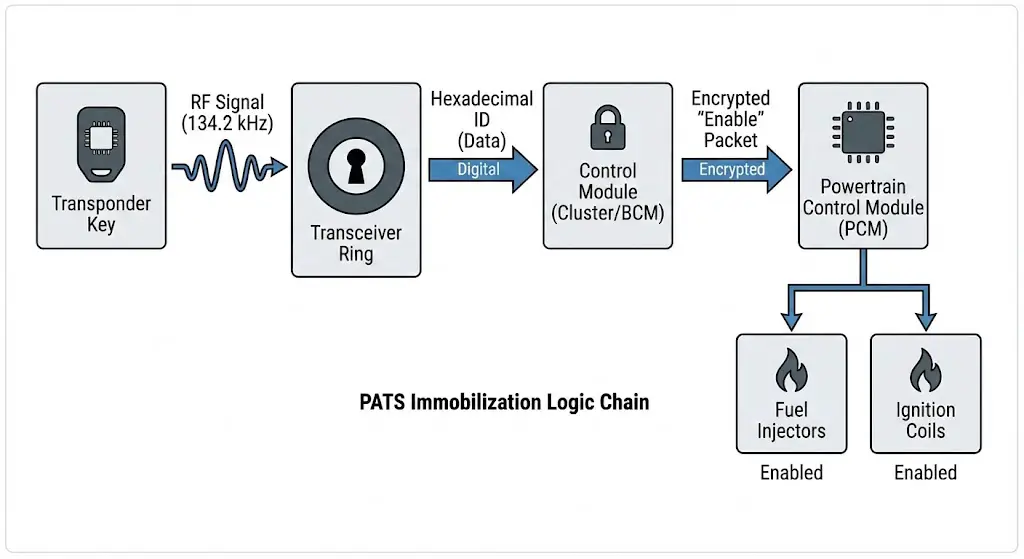
The immobilization sequence is a strict logic gate:
- Excitation: Ignition ON energizes the transceiver.
- Read: Transceiver reads the key's 40-bit or 80-bit ID.
- Verification: The Control Module (e.g., Cluster) compares the ID against its NVRAM "Allowed Key List."
- Handshake:
- If Match: The Control Module sends an encrypted "Enable" packet to the PCM.
- If No Match: The Control Module sends a "Disable" packet (or sends nothing), and the PCM maintains fuel injector cutoff.
- Execution: The PCM fires the injectors and ignition coils.
If any component in this chain fails—corrupted data on the CAN bus, a broken transceiver coil, or a non-programmed key—the system defaults to a secure state (engine disabled).
The Myths of Analog Bypassing
In the realm of automotive forums and DIY discussions, misinformation regarding PATS bypassing is rampant. The most persistent of these is the "Resistor Hack."
The "Resistor Hack" Fallacy
The resistor hack involves cutting the wires leading to the ignition cylinder and splicing in a specific resistor value. This method is legitimate for General Motors vehicles equipped with the VATS (Vehicle Anti-Theft System) from the 1980s, where the key contained a simple resistor pellet. The car's computer measured the voltage drop across the key; if it matched the stored value, the car started.
Why it fails on Ford PATS:
Ford's system is digital, not analog. The wires connecting the transceiver to the control module (typically four wires: Power, Ground, TX, and RX) carry complex digital data streams, not static resistance values.8
- TX (Transmit): Sends a digital query (Challenge) to the key.
- RX (Receive): Carries the hexadecimal response from the key.
Attempting to splice a resistor into the RX/TX lines will effectively short the data bus or pull the voltage to a fixed level, corrupting the signal. This will trigger a specific Diagnostic Trouble Code (DTC) such as B1681: PATS Transceiver Signal Not Received and result in a rapid-flashing theft light.4 The PCM expects a data packet, not a resistance value; no amount of resistors can simulate a 40-bit encryption key.
The Fuel Pump Hardwire Myth
Another common desperate measure is attempting to "jump" the fuel pump directly from the battery or fuse box, bypassing the fuel pump relay.
- Result: The fuel pump will run, pressurizing the fuel rail.
- Outcome: The engine will still not start.
- Reason: The PATS system disables the fuel injectors at the PCM level. Even with 50 PSI of fuel pressure at the rail, the injectors will not pulse without the PCM's command. In later generations, the system also disables the spark plugs and the starter motor.
The Battery Disconnect Reset
A widely circulated myth suggests that disconnecting the vehicle's battery for 30 minutes to overnight will "reset" the anti-theft system and allow the car to start.
- Reality: The "Allowed Key List" is stored in Non-Volatile Random Access Memory (NVRAM) or EEPROM. This type of memory retains data even without power, similar to a USB flash drive. Disconnecting the battery may clear "Keep Alive Memory" (KAM) such as fuel trim adaptations or temporary error codes, but it will never erase the security programming. If the battery reset worked, vehicle theft would be trivially easy.
Diagnostic Protocols and Failure Analysis
Before assuming a key programming issue, it is imperative to perform a forensic diagnosis of the system using the vehicle's built-in indicators.
The Theft Light Oracle
The "Theft" or "Security" light on the dashboard is the primary communication interface for the PATS system. Its behavior provides specific error codes that guide the technician.
- Normal Behavior:
- Ignition OFF: Flashes once every 2 seconds (visual deterrent).
- Ignition ON: Glows solid for 3 seconds, then extinguishes (System passed, key verified).
- Failure Behavior:
- Rapid Flashing: Upon turning the ignition, the light flashes rapidly. This indicates a system failure or an unrecognized key.
- Flash Codes: If left to flash rapidly for approximately 45-60 seconds, the light will pause and then blink a 2-digit code (LFC - Lamp Flash Code).
Common Flash Codes:
- Code 11: Transceiver not connected or circuit open. (Check wiring at the steering column).
- Code 13: No key data received. (Key transponder is dead or key is blank).
- Code 14: Part of the key code received. (Transponder is damaged or incompatible format).
- Code 15: Key code received but invalid. (Key is good but not programmed to this car).
- Code 16: CAN bus communication failure. (PCM and Cluster cannot talk; common in older F-150s with instrument cluster solder fractures).
Hardware Troubleshooting
For Code 11 or 16, physical inspection is required before attempting software bypasses.
- Transceiver Coil: Use a multimeter to measure resistance across the transceiver coil pins. An open circuit (infinite resistance) indicates a broken winding, requiring replacement of the transceiver ring.8
- Instrument Cluster (HEC): On models like the 1999–2004 Mustang and F-150, the PATS logic board inside the cluster often develops cold solder joints at the harness connector. Reflowing these solder points can often resolve a permanent "Theft" condition without needing new keys.
Software-Based Bypass and Recovery (The Authorized Path)
In an "All Keys Lost" (AKL) scenario—where no working master key is present to authorize the addition of spares—the only engineered solution is to interface with the control module and reset the key memory. This is not a "bypass" in the sense of tricking the system, but rather a "reset" that restores legitimate access.
FORScan: The DIY Industry Standard
FORScan has democratized access to Ford's proprietary diagnostic protocols. What once required a $5,000 Ford IDS (Integrated Diagnostic System) setup can now be accomplished with a laptop and a $50 OBDII adapter.
Required Hardware and Licensing
To perform PATS operations, the user requires:
- Software: FORScan for Windows (PATS programming is generally not supported on the mobile "Lite" versions).
- License: An Extended License is mandatory to access the "Service Functions" tab where PATS operations reside. This license is generated via the FORScan forum and requires registration.
- Adapter: A high-quality J2534 or ELM327 adapter. The recommended units are the OBDLink EX or vLinker FS, which support automatic switching between High-Speed (HS-CAN) and Medium-Speed (MS-CAN) networks, essential for communicating with both the PCM and BCM.18
The "Erase All Keys" Procedure

When zero keys are available, the user must wipe the slate clean.
- Connection: Connect the vehicle to FORScan.
- Access: Navigate to
Service Functions>PATS Programming(orPATS Servicedepending on model). - Security Access (Coded Access): Upon selecting "Erase All Keys," the system will initiate a security countdown. This is a hard-coded 10-minute delay (sometimes 12 minutes) mandated by Ford engineering to prevent "smash and grab" diagnostic thefts. The ignition must remain ON, and the laptop must not sleep during this window.
- Note: FORScan manages the "Incode/Outcode" exchange automatically for most models up to 2011. For some models, it may prompt for an Incode, which can be generated using external calculators.
- Wipe and Relearn: Once access is granted and keys are erased, the system enters "Learn Mode."
The Two-Key Requirement
A critical constraint of the Ford PATS logic is the Two-Key Rule. After an "Erase All Keys" reset, the system will remain in a theft state (preventing the engine from starting) until it successfully reads two unique transponder IDs.
- Implication: A user cannot simply buy one replacement key. They must possess two mechanically cut keys with valid chips.
- Procedure:
- Insert Key 1, turn to ON for 3 seconds, turn OFF.
- Insert Key 2, turn to ON for 3 seconds, turn OFF.
- The system compares the two IDs. If they are unique and valid, the PID
MIN_KEYS_REQUIREDis satisfied, and the engine is enabled.
- Insight: Attempting to use the same key twice or using a "cloned" key (where Key 2 is a digital copy of Key 1) will fail, as the system demands unique hexadecimal signatures.
Professional Locksmith Tools
Automotive locksmiths utilize dedicated hardware such as the Autel MaxiIM IM608, Smart Pro, or XTool AutoProPad.
- Advantages: These tools can often bypass the 10-minute wait time on older systems. More importantly, on newer vehicles (2015+), they can sometimes force a "Parameter Reset" or satisfy the system with a single key if the software supports "Skip 2nd Key" functions.
- Cost vs. Capability: While FORScan is virtually free (excluding the adapter), professional tools cost thousands. However, for 2021+ models utilizing the new Ford alarm structures, FORScan's capabilities are limited, and professional tools with NASTF (National Automotive Service Task Force) credentials may be required.
Hardware Bypass Modules (The Remote Start Solution)
For vehicle owners looking to install remote starters or permanently bypass the immobilizer without repairing the factory key system, aftermarket interface modules offer a sophisticated hardware solution.
Data-Override Architectures
Modern bypass modules from manufacturers like Fortin (EVO-ALL) and Directed Electronics (DB3, XK04) operate by interfacing directly with the vehicle's digital data bus.
- Wiring: These modules connect to the PATS TX and RX wires (interception) and the CAN High/Low wires.
- Function: They listen to the PCM's challenge and replay a valid key code.
The "No Key" DCryptor Technology
The "All Keys Lost" scenario poses a problem for bypass modules: typically, you need a working key to "teach" the module. However, Fortin developed a technology called DCryptor to overcome this.
- The Process:
- Sniffing: The unprogrammed module is installed in the vehicle.
- Data Capture: The ignition is turned (even with a non-chip key). The module captures the "Challenge" signal sent by the vehicle's PCM. Since there is no key to answer, the car doesn't start, but the module now has the cryptographic question.
- Server Calculation: The user connects the module to a PC using a FlashLink Updater. The captured data is uploaded to Fortin's servers.
- Decryption: The server uses massive computing power to brute-force or calculate the correct response for that specific PCM challenge, effectively generating a "Virtual Key."
- Injection: This virtual key is downloaded back to the module.
- Emulation: The module is reinstalled. When the remote start is triggered, the module answers the PCM's challenge with the server-calculated response. The car starts without a physical key ever being present.
Emergency and Physical Hacks
In desperate situations where software or hardware modules are unavailable, crude physical bypasses exist. These are generally not recommended due to security risks but are technically functional.
Transponder Relocation (The "Gluing" Method)
If a user has a key with a broken blade but a working chip, or a "valet" key that works but they want to use cheap $2 metal keys, they can perform a permanent bypass.
- Extraction: The transponder chip is carefully removed from the working key's head (often requiring cutting the plastic).
- Placement: The chip is taped or glued directly onto the plastic shroud of the steering column, close to the transceiver ring.
- Testing: The user attempts to start the car with a non-chipped key. The transceiver reads the glued chip, validates it, and allows the engine to start.
- Risk: This permanently disables the immobilization feature. Any key that turns the lock (or a screwdriver forcing the lock) will now start the vehicle.
The "Coffin" Box (556U)
An older style of bypass involves a "Universal Interface Module" (often called a coffin box).
- Method: A valid spare key is placed inside a small box installed under the dashboard. A wire antenna from the box is wrapped around the ignition cylinder.
- Operation: When the remote start activates, the box energizes the key inside it and relays the RF signal to the ignition cylinder antenna.
- Pros: Does not require complex data programming.
- Cons: Requires sacrificing a working key. If a thief finds the box, they have a key to the car.
Legal, Insurance, and Warranty Implications
The decision to bypass a factory security system transcends engineering; it enters the domain of liability and contract law.
Insurance Claim Denials
Automobile insurance policies invariably contain clauses regarding the maintenance of factory security systems.
- Theft Claims: If a vehicle is stolen and recovered, forensic analysis may reveal that a transponder was glued to the column or the immobilizer was bypassed. Insurers can deny the claim based on "Material Misrepresentation" or "Failure to protect the insured property".
- Forcible Entry Clauses: As seen in cases like Offutt v. Liberty Mutual, some policies require visible signs of forcible entry. A bypassed PATS system allows a thief to drive away without typical "hotwiring" damage, potentially complicating the proof of theft.
Warranty Voiding
Under the Magnuson-Moss Warranty Act, a manufacturer cannot void a warranty simply because an aftermarket part (like a remote start bypass) is installed. However, if the installation of the bypass module involves splicing into the CAN bus and subsequently causes an electrical failure (e.g., frying the BCM), the warranty claim for that specific repair can be validly denied. The burden of proof lies with the dealer, but spliced wiring is often sufficient evidence of "tampering".
Model-Specific Case Studies and Data
Ford F-150 (2004-2008)
This generation is notorious for "Code 11" and "Code 16" errors not due to keys, but due to the location of the PATS transceiver wiring. The harness runs through the steering column tilt mechanism, leading to chafing and open circuits. A bypass (software or hardware) will not fix this; the physical wiring must be repaired.
Ford Ranger (PATS II)
The Ranger maintained the older PATS II system longer than most models (up to 2011). It is one of the easiest vehicles to program using FORScan as it typically uses standard Texas Instruments 4D-63 chips and has a robust, simple handshake protocol. It serves as an excellent entry point for learning PATS programming.
2013+ Ford Fusion / Escape (PATS IV/V)
These vehicles introduced high-security keys (laser cut) and integrated the PATS logic into the BCM with tighter integration to the Remote Keyless Entry. The "All Keys Lost" procedure on these models is significantly riskier with FORScan; an interruption during the BCM programming can "brick" the module, rendering the car completely dead. Professional tools with stable power supplies (battery maintainers) are highly recommended here.
The End of DIY Bypassing?
Newer security architectures utilize 128-bit AES encryption and real-time server-side verification for key programming (requiring NASTF VSP credentials). This is closing the door on simple DIY tools like FORScan for newer models, pushing the "All Keys Lost" solution back toward the dealership and certified professionals.
Conclusion
The quest to bypass the Ford PATS system reveals a complex interplay of physics, digital logic, and automotive history. The "Resistor Hack" is a relic of a bygone analog era, inapplicable to the digital precision of SecuriLock. For the modern vehicle owner facing an "All Keys Lost" scenario, the path of least resistance—and highest reliability—is not a bypass, but a system reset using tools like FORScan. This method restores the vehicle to factory specifications without compromising its security or insurability.
While hardware modules like the Fortin EVO-ALL offer a fascinating "No Key" loophole via server-side decryption, they represent a significant technical investment best suited for remote start installations rather than simple key recovery. Ultimately, as automotive security evolves into the cloud, the days of hotwiring and physical bypasses are drawing to a close, underscoring the critical importance of maintaining duplicate keys and understanding the digital heartbeat of one's vehicle.








